Document
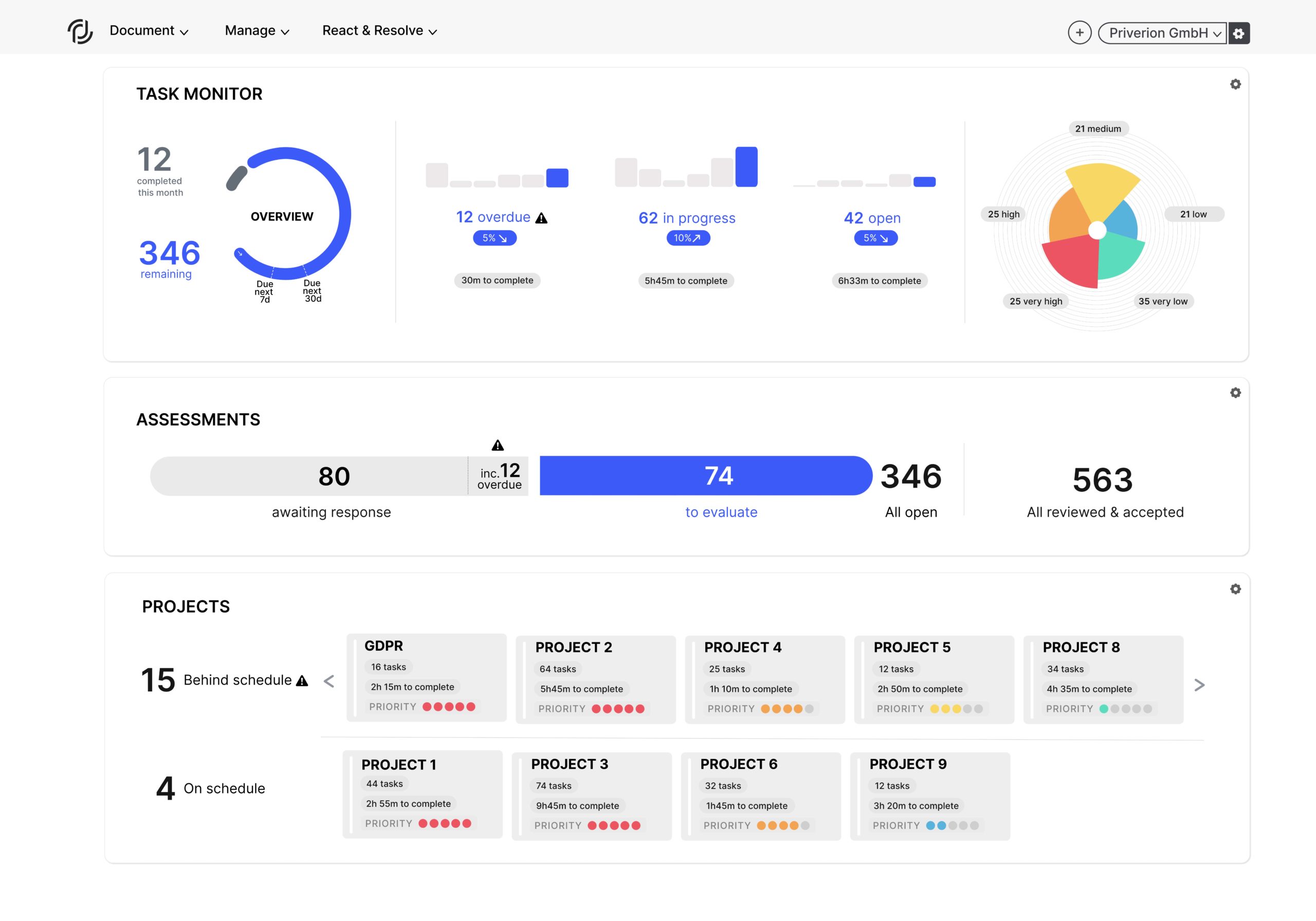
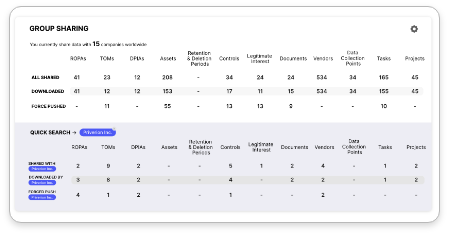
One place to gather the documentation for your Privacy and Information Security programs. From the Record of Processing Activities with a process based risk view to the Asset Register with an asset based risks view you are covered from all angles.